Swipe left or right to navigate to next or previous post
Content Security Policy (CSP) in inline styles and scripts
25 Nov 2024
. category:
Programming
.
Comments
#Programming
#Frontend
#JavaScript
#Security
#Backend
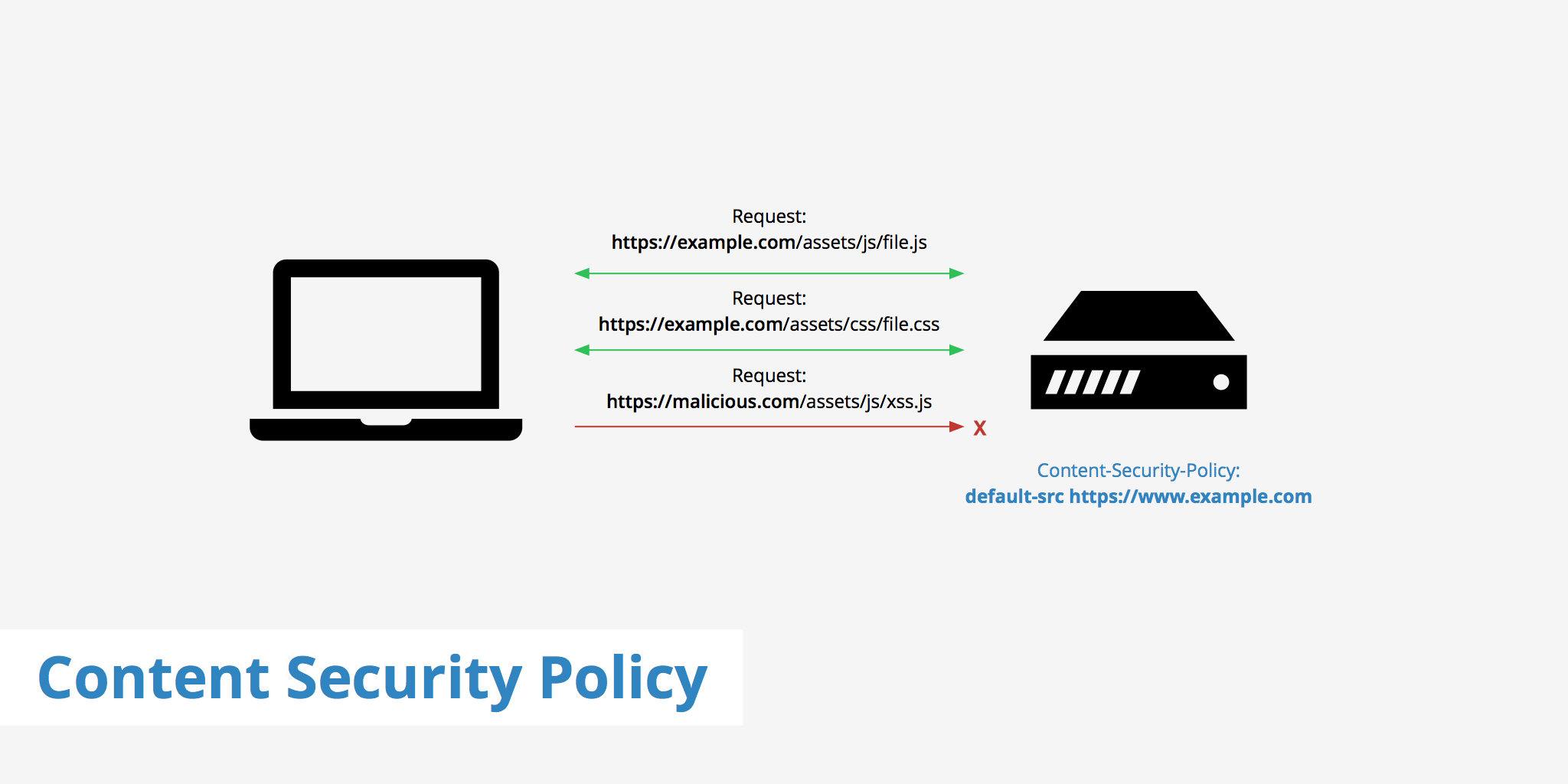
Content Security Policy (CSP) is an essential security feature that protects websites from cross-site scripting (XSS) and other injection attacks by specifying which sources of content are trusted. By focusing on scripts and styles, CSP can significantly reduce attack surfaces, ensuring only authorized scripts and styles are executed or rendered. This in-depth guide explores the details and nuances of applying CSP to scripts and styles.
One of the challenges developers face when implementing Content Security Policy (CSP) is managing inline scripts (JavaScript embedded directly in HTML) and inline styles (CSS written within HTML tags). CSP blocks these by default to protect your website from Cross-Site Scripting (XSS) attacks. However, in some cases, inline code might be necessary, and CSP provides secure mechanisms to handle them effectively.
1. CSP for Scripts
Scripts are a critical part of web applications but also a common target for XSS attacks. CSP provides mechanisms to restrict and validate the sources and types of scripts allowed on a webpage.
Why Inline Scripts and Styles Are Blocked
Inline scripts and styles are inherently risky for several reasons:
- XSS Vulnerability: Attackers can inject malicious code directly into your pages.
- Harder to Trace: Inline code lacks a clear source, making it difficult to audit or verify.
- Weak Content Control: Without restrictions, any inline script or style, even malicious ones, can execute.
CSP avoids these risks by blocking all inline scripts and styles unless explicitly allowed.
The script-src Directive
The script-src directive controls which script sources are allowed to load. This directive can include:
'self': Allows scripts from the same domain as the page.- Specific URLs: For example,
https://trusted.cdn.com. - Nonces: Tokens generated dynamically and added to inline scripts.
- Hashes: Cryptographic hashes of script content.
- Keywords: Such as
'unsafe-inline'(not recommended) or'unsafe-eval'(should be avoided).
Example policy:
Content-Security-Policy: script-src 'self' https://trusted.cdn.com;
Handling Inline Scripts with Nonces
Inline scripts are inherently risky but can be securely allowed using nonces. A nonce (short for "number used once") is a unique, randomly generated token that allows specific inline scripts to run. Her. For example:
-
Generate a Unique Nonce: Your server should generate a random token for every page load and include it in the CSP header.
const nonce = uuid.v4(); Content-Security-Policy: script-src 'self' 'nonce-abc123'; -
Add the Nonce to Inline Scripts: Use the same nonce in your inline script tag.
# If the nounce value is abc123, it can be written in script as <script nonce="abc123"> console.log('This inline script is secure.'); </script>
Nonces must be regenerated for each request, ensuring that they cannot be reused in replay attacks. The browser checks that the nonce in the script tag matches the one in the CSP header. If they match, the script executes; otherwise, it is blocked.
Allowing Inline Styles Using Nonces
You can also use nonces for inline styles:
-
Add Nonce to CSP Header: Specify the nonce for styles in the header.
Content-Security-Policy: style-src 'self' 'nonce-def456'; -
Include the Nonce in Inline Styles:
<style nonce="def456"> body { background-color: #f0f0f0; } </style>
Allowing Inline Content Using Hashes
Another option is using a hash. The hash is a cryptographic value calculated from the content of the inline script or style. If the content matches the hash, the browser allows it to run.
-
Calculate the Hash: For example, if your inline script is:
Calculate its SHA-256 hash (using a tool or library). The hash might look like:<script> console.log('Hello, World!'); </script>sha256-xyz123... -
Add the Hash to CSP Header:
Content-Security-Policy: script-src 'self' 'sha256-xyz123...'; -
No Additional Attributes Needed: Include the inline script as usual:
<script> console.log('Hello, World!'); </script>
Best Practices for Handling Inline Content
Inline scripts and styles are convenient but introduce security risks, making them a prime target for cross-site scripting (XSS) attacks. To mitigate these risks, adopting best practices when working with inline content is essential. Here’s a detailed guide to managing inline content securely:
-
Avoid Inline Scripts and Styles:
Inline scripts and styles are inherently risky because they bypass traditional CSP protections unless explicitly allowed. Whenever possible:
- Move JavaScript code to external files and reference them via a
scripttag with a trustedsrcattribute. - Define CSS in external stylesheets or using
linktags pointing to trusted sources.
This approach not only enhances security but also improves maintainability by separating content from logic and design.
- Move JavaScript code to external files and reference them via a
-
Use Nonces for Dynamic Content:
If inline content is unavoidable (e.g., dynamically injected JavaScript or CSS), use nonces to secure it. Nonces are unique, randomly generated tokens added to the CSP header and inline tags:
Content-Security-Policy: script-src 'self' 'nonce-xyz123';Remember to regenerate nonces for every request to prevent reuse in replay attacks.
-
Use Hashes for Static Content:
For static inline scripts or styles that rarely change, hashes provide a robust alternative to nonces. A hash is a cryptographic representation of the content, ensuring that only the intended script or style is executed. To use hashes:
- Calculate the hash of the inline content using a secure algorithm like SHA-256:
- Include the hash in your CSP policy:
- Ensure that any change to the inline content updates the hash in the CSP header.
echo -n "console.log('This is a static inline script.');" | openssl dgst -sha256 -binary | openssl base64Content-Security-Policy: script-src 'self' 'sha256-BASE64_ENCODED_HASH'; -
Audit Your Inline Content:
Periodically review all inline scripts and styles in your application to determine:
- Are they necessary?
- Do they contain any potentially insecure functionality (e.g., usage of
eval()or dynamic code injection)? - Can they be moved to external files for better control?
Regular audits ensure that your CSP policies remain relevant and effective.
-
Monitor Violations:
CSP violations occur when scripts or styles are blocked due to policy restrictions. Monitoring these violations helps identify misconfigurations or potential attack attempts. Use the
report-uriorreport-todirective to collect violation reports:Content-Security-Policy: script-src 'self'; report-uri /csp-violation-report;Example violation report endpoint response format:
{ "csp-report": { "document-uri": "https://example.com", "referrer": "", "violated-directive": "script-src 'self'", "blocked-uri": "https://untrusted.example.com", "original-policy": "script-src 'self';" } }Analyze these reports to refine your policies and ensure compliance with your security goals.
By following these best practices, you can minimize the risks associated with inline content and leverage CSP to its full potential, protecting your users and application from XSS and other injection-based attacks.
Want to Explore more on Content security policy - A Shield Against Modern Web Vulnerabilities, Please visit
